EXTENSIVE PROTECTION FROM ADVANCED
CYBER THREATS
Made Easy.
Simply put, we constantly make it harder for threats to compromise your people and IT infrastructure. If an attack does slip through, we’ll detect it before damage is done.
We’ll also make sure you pass your audit.
And… we do everything possible to keep it painless, keep it easy.
RADICL XTP provides strong, enterprise-grade cybersecurity
With RADICL, SMBs can realize a level of protection previously reserved to large enterprises able to purchase best-in-breed technologies supported by large teams of expert operators.
We’ve changed the formula. Using our proprietary, AI-Augmented XTP Platform, RADICL becomes your expert security operations team.
That’s right. 100% managed. By us. For you. We leverage analytics, automation, and AI to deliver strong, enterprise-grade cybersecurity that SMBs can actually afford and deliver:
- Threat Management
- Attack Surface Management
- Compliance Management
- Managed Security Operations
Made Easy. Made Affordable.
.png?width=600&height=614&name=RADICL_XTP_Principal%20(1).png)
CUSTOMER FOCUS: Barn Owl's Security Posture Vastly Improved
“RADICL’s comprehensive approach to cyberthreat protection and mitigation–from threat hunting to effective phishing simulations and vulnerability management workflow–has vastly improved our overall security posture.”
THREAT MANAGEMENT
Protecting the fast-evolving IT infrastructure is a daunting task - particularly if you don’t have dedicated staff to focus on. All. The. Time. We leverage best-in-class technology to protect your infrastructure and mobile perimeter from known threats. We leverage our deep-spectrum™ analytics to detect novel and deeply embedded threats. We are ready to respond 24x7 should an attack get through. Our platform never tires, our people are ever vigilant.
XTP:ENDPOINT, XTP:HUNT, and XTP:RESPOND provide:
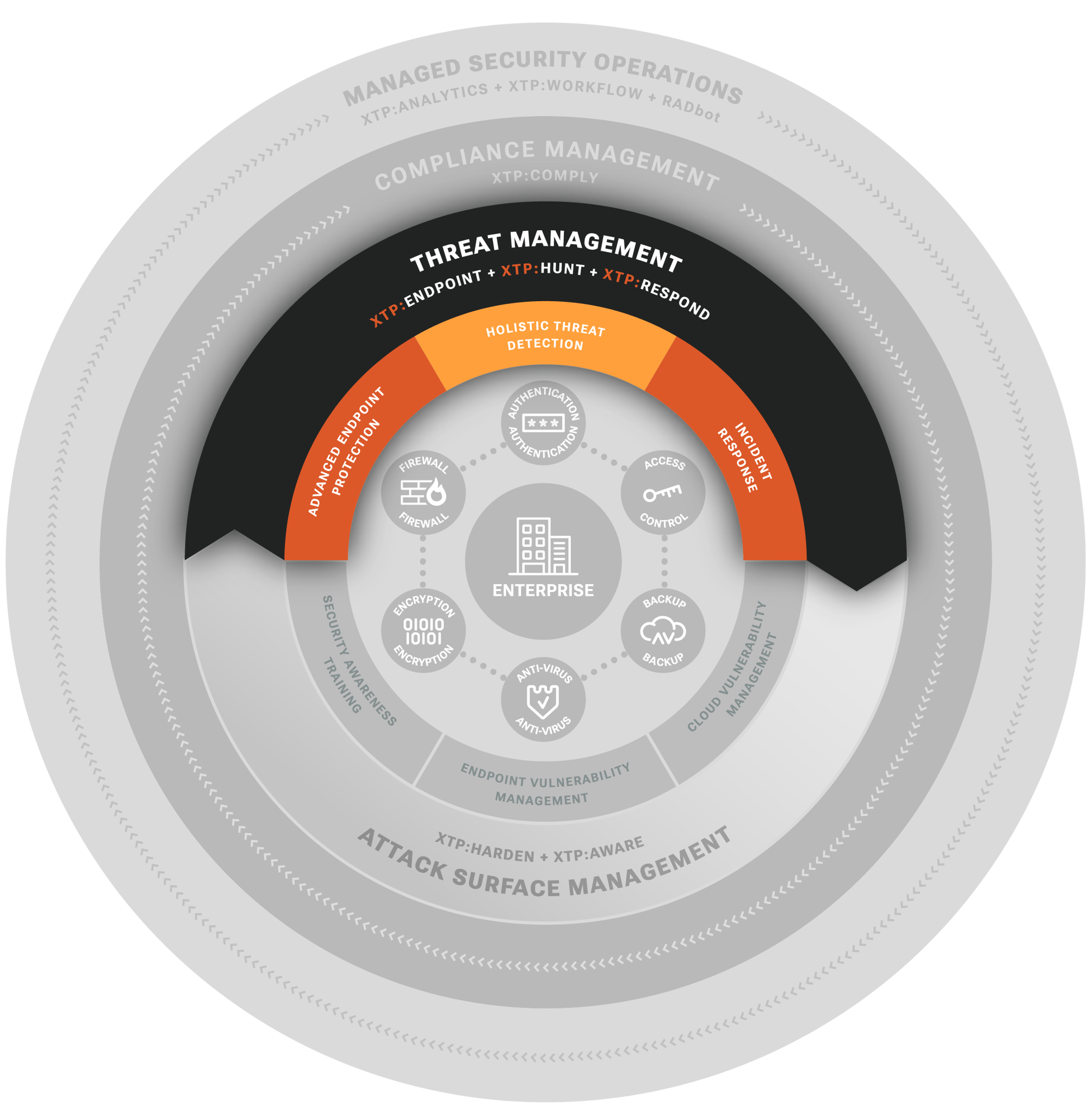
Advanced Endpoint Protection
Managed operation of best-in-breed endpoint protection technology to ensure most attacks are blocked and compromises are avoided.
Deep-Spectrum™ Threat Detection
Leverages environmental visibility, machine analytics, and expert-driven hunting to detect novel attacks and deeply embedded threats.
24 x 7 Threat Monitoring
Around-the-clock monitoring and investigation into indicators of compromise ensuring sophisticated attacks don't go unnoticed.
24 x 7 Incident Response
Fast containment and mitigation that reduces operational impact and risk if an advanced attack slips through.
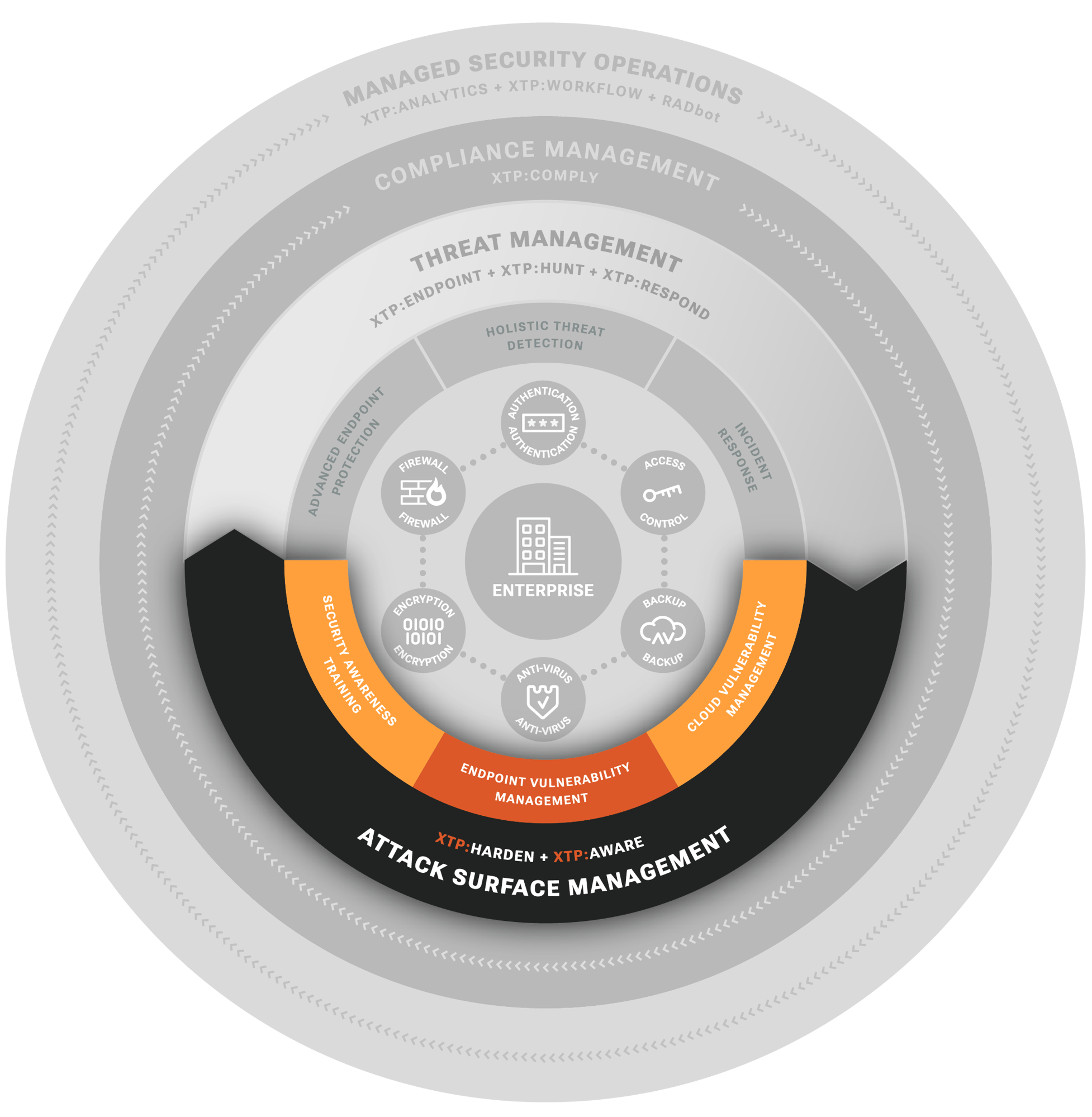
ATTACK SURFACE MANAGEMENT
Understanding and closing avenues of attack is the essence of attack surface management. Make it harder for a threat to gain a footing, and they may eventually give up. If they are the truly persistent type (e.g., nation-state APT), attack surface management is critical to slowing them down long enough so that they can be detected. We make our customers less likely to give ground, and harder for a threat to gain ground if operating from within.
XTP:HARDEN, and XTP:AWARE provide:
Vulnerability Awareness
Identification of system and software vulnerabilities across the extended IT infrastructure and mobile perimeter.
Security Awareness Training
Reduced risk of human error resulting in system and account compromise through phishing simulations and training exercises.
Remediation Operations
Intelligent prioritization of which vulnerabilities to fix first with expert guided assistance and resolution verification.
P1 Issue Response
Rapid response when critical vulnerabilities are identified that could lead to immediate compromise or operational risk.
COMPLIANCE MANAGEMENT
We’ve got you covered when it comes to Compliance. Our experts understand regulations like CMMC Level 1, CMMC Level 2, and NIST 800-171 and what it takes to pass an audit. We demystify this complex and confusing world and provide actionable forward direction to incrementally bring you into compliance. On top of that, our offering directly addresses some of the hardest and most costly requirements to realize compliance. For the remaining requirements, we become your trusted wingman, ensuring by audit time, you are prepared to pass.
XTP:COMPLY provides:
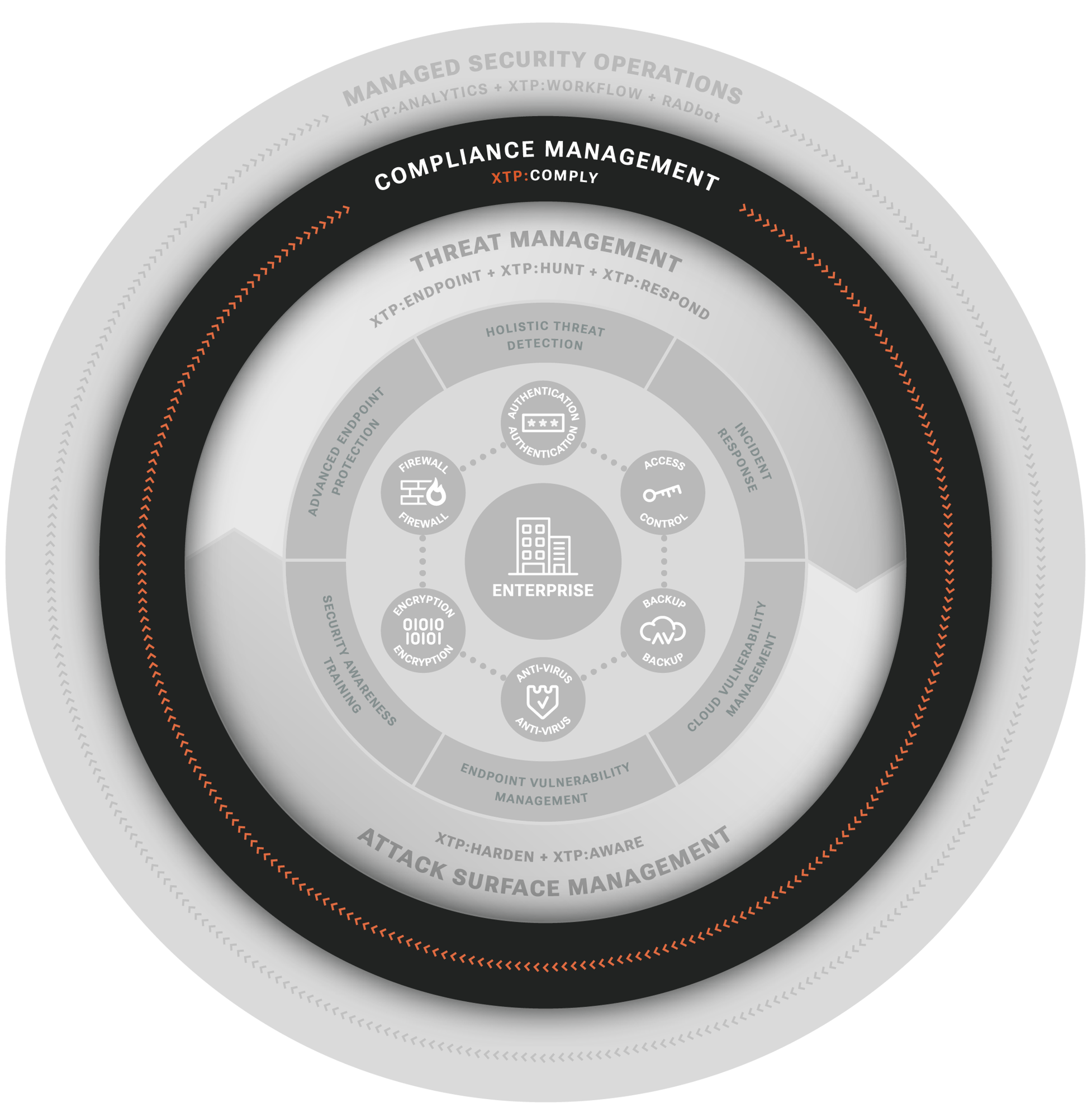
Framework Comprehension
A complete understanding of framework requirements and what must be done to meet them.
Current Posture Assessment
Current and continuously updated perspective on compliance coverage, gaps, and risks.
Adherence Operations
Prioritized tasks and expert guidance for adherence, whether work is performed by you or your MSP.
Audit Preparedness
Compilation of evidence that helps expedite audits and ensure compliance verification.
AI-AUGMENTED MANAGED SECURITY OPERATIONS
Delivering Threat Management, Attack Surface Management, and Compliance Management requires expertise and people power. Our people are powered by the most powerful security analytics and operations platform in the planet - at least in our humble opinion. Our experts, powered by the RADICL XTP Platform, become your security operations team. AI, analytics, and automation allow us to get work done fast on your behalf. If we or RADbot can’t get it done, our workflow engine automatically routes work to the appropriate party, with expert guidance on what to do and how.
XTP:ANALYTICS, XTP:WORKFLOW, and RADbot provide:
.png?width=1954&height=2000&name=RADICL_XTP-MSO%20(1).png)
24 x 7 Tireless Operations
Our automated analytics and workflow is tireless. RADbot never sleeps. Our experts are at the ready 24x7 when human hands are needed.
Transparent Operations
Real-time and complete visibility into all work being performed by RADbot or the RADICL vSOC on your behalf.
Secure Collaboration
In-platform information sharing and collaboration that is safe from malicious eyes in the event your environment is deeply compromised.
Expert Guidance
When work or help is asked of you, we ensure you are armed with what to do and how to do it, reducing confusion, speeding response.
“RADICL’s weekly bespoke threat hunting operations and deep analytics across our infrastructure are a valuable addition to Red6’s IT security framework and help ensure that we are confidently secure from advanced threat actors.”