CMMC Level 2
“Besides guiding our CMMC 2.0 compliance journey, RADICL has drastically improved our security posture and helps ensure that identified vulnerabilities are quickly mitigated by continually hardening our environment.”
RADICL Will Expertly Guide You Through your CMMC Journey
RADICL knows what’s required to comply with CMMC Level 2. We also understand that compliance is an ongoing journey and takes time. Our vSOC will patiently guide and periodically nudge you into full compliance. On top of that, RADICL XTP directly or partially meets 37% of CMMC Level 2 requirements. Once onboarding and operating you'll already be well on your way.
CMMC Level 2 Basics
The Cybersecurity Maturity Model Certification (CMMC) is a program developed by the U.S. Department of Defense (DoD) to ensure that contractors and subcontractors protect Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) that is shared with them through acquisition programs.
Small-to-medium-sized businesses (SMBs) in the Defense Industrial Base (DIB) know it well and most are wrestling with how, and when, they’ll manage their compliance with it.
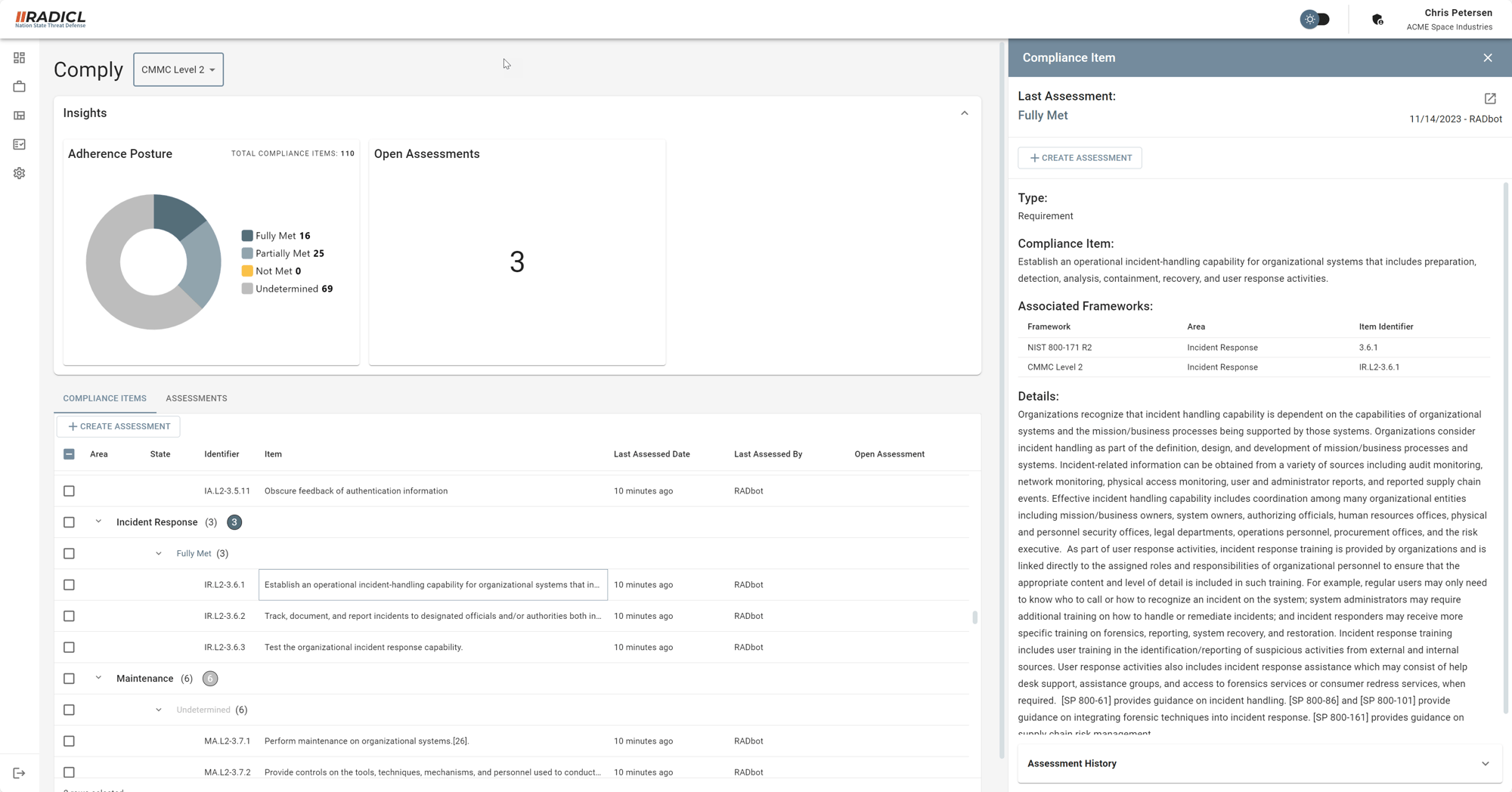
Cybersecurity Maturity Model Certification (CMMC) has three levels of cybersecurity: Basic, Advanced, and Expert. Each level has a set of practice areas and controls that organizations need to implement in their operations and management.
Level 2 is the Advanced level of cybersecurity for organizations that handle Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) for the U.S. Department of Defense (DoD). It requires 110 controls across 17 practice areas that are based on the NIST SP 800-171 guidelines. Some of the controls introduced in Level 2 are:
-
Implementing multi-factor authentication for network access [Identification and Authentication (IA)]
-
Monitoring and controlling remote access sessions [System and Communications Protection (SC)]
-
Encrypting CUI on mobile devices and removable media [Media Protection (MP)]
-
Developing and implementing plans of action designed to correct deficiencies and reduce or eliminate vulnerabilities in organizational systems [Security Assessment (CA)]
-
Providing security awareness training to personnel, including role-based training [Awareness and Training (AT)]
Additional CMMC resources: