THE PLANET'S MOST POWERFUL MANAGED SECURITY ANALYTICS AND OPERATIONS PLATFORM
Enterprise-grade cyberthreat protection for SMBs. We deliver the world's most capable security operations and analytics platform as a fully managed virtual SOC (vSOC). By deeply leveraging AI and automation, we make capabilities once reserved for large enterprises accessible and affordable for smaller security teams.
The RADICL Xperience
RADICL Becomes Your Security Operations Team, Quickly and Seamlessly.
We are architected from the ground up with the principal goal of uniquely harnessing artificial intelligence (AI) towards workflow automation and advanced threat detection. Our platform unifies SIEM/XDR analytics, incident response, vulnerability reduction, and compliance evidence in one place, then uses automation to handle the heavy lifting.


Initial Consultation
We start with an honest conversation about your security posture, compliance requirements, and whether RADICL is the right fit. No pressure, no overselling, just a straightforward assessment of how we can help.

7-Days Deployment
Once we kick off, we work fast. EDR sensors deploy, identity integrations connect, custom detection analytics tune to your environment. Within a week, your virtual SOC is monitoring 24/7 with threat hunting and incident response ready.

Continuous Ops
Vulnerability prioritization with verified remediations. Continuous threat hunting and detection refinement. Regular compliance reviews to maintain audit readiness. Dashboard visibility into all operations with routine check-ins.
Our Core Security Operations Platform Capabilities
The RADICL platform delivers enterprise-grade security operations through integrated managed services. AI precision with human expertise: autonomous digital agents execute continuous operations while expert analysts verify findings and provide strategic oversight. Our virtual SOC becomes your security and compliance team, driving proactive protection across your entire IT environment.

MDR | Endpoint
Best-in-breed EDR technology with fully managed deployment, custom detection analytics, and weekly Deep Spectrum threat hunts. 24/7 monitoring, investigation, and incident response ensure threats are contained within minutes, not hours or days.

MDR | Identity
Real-time monitoring of authentication sessions, privileged access, and identity platforms. Custom detection analytics identify account takeovers, business email compromise, and credential abuse before they escalate into ransomware or data theft.

MAS | Managed Attack Surface
Risk-prioritized vulnerability remediations based on exploitability, threat intelligence, and client-specific context. Expert-provided step-by-step instructions with closed-loop verification ensure high-risk exposures get fixed before attackers exploit them.

MSA | Managed Security Awareness
Annual courseware, biweekly training snippets, and continuous phishing simulations with on-the-spot remediation training. User risk visibility and completion tracking ensure your team reduces human vulnerability and remain compliant.

MCA | Managed Compliance Adherence
Weekly guided self-assessments with expert compliance consultants who provide remediation instructions, spot-check evidence, and ensure audit readiness. Comprehensive documentation templates and consolidated evidence management eliminate the chaos of compliance preparation.

vSOC | Virtual SOC
24/7 operations across endpoint, identity and network infrastructure with complete incident ownership from alert triage through containment and recovery. Expert-driven threat hunting, vulnerability operations, compliance management, and security awareness programs delivered through unified platform visibility.
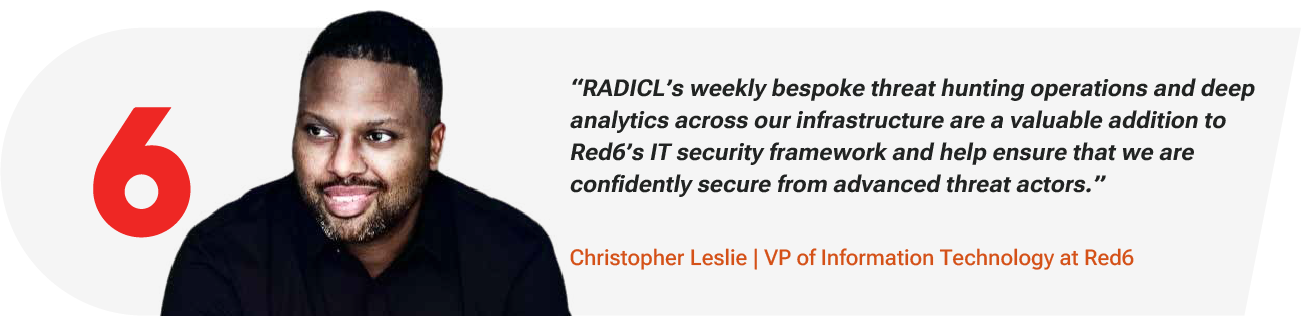
CMMC and NIST 800-171 Readiness, Built Into Our Platform
RADICL's Managed Compliance Adherence directly addresses 29 of the 110 CMMC Level 2 controls. While guiding weekly self-assessments with expert remediation and Level 2 audit-ready evidence. Platform-maintained SPRS scoring and quarterly reviews keep you compliant between audits. Make compliance sustainable, not a one-time scramble.
Self-Assessment Tools
Easily evaluate your compliance status
Guided Gap Remediation
Step-by-step instructions to close gaps
Documentation Support
Generate required evidence effortlessly
Live Progress Tracking
Real-time visibility into your compliance journey
Integrations and MSP Collaboration
Built to Coexist with Your Stack and Your MSP
Integrates with leading EDR (CrowdStrike, SentinelOne, Defender), identity providers (M365, Google Workspace, Entra ID), network infrastructure, and ticketing systems. Correlates signals across technologies in entity context, connecting endpoint, identity, and network activity.
Coordinates remediation through secure workflows. MSPs execute detailed remediation tasks with closed-loop verification. We provide specialized security expertise and 24/7 operations while your MSP handles infrastructure. No vendor competition or blame games. Just better outcomes.




AI and Entity-Oriented Data Fabric
Pervasive Application of AI
AI powers decision accuracy, automates containment and enrichment, and detects advanced, multi‑stage threats. By moving from human speed to software speed, our platform reduces noise, prioritizes what matters, and shortens time to detect and respond.
Because AI handles so much of the triage and investigation work, you get enterprise‑level vigilance without having to staff a full in‑house SOC.

Intelligence Starts with Data Quality
Our proprietary Entity‑Oriented Data Fabric models users, devices, identities, applications, and their relationships. This normalized, entity‑aware context is the foundation for high‑precision analytics, high‑recall automation, and efficient investigations across your environment.


Intelligence Starts with Data Quality
Our proprietary Entity‑Oriented Data Fabric models users, devices, identities, applications, and their relationships. This normalized, entity‑aware context is the foundation for high‑precision analytics, high‑recall automation, and efficient investigations across your environment.
Intelligence Starts with Data Quality
Our proprietary Entity‑Oriented Data Fabric models users, devices, identities, applications, and their relationships. This normalized, entity‑aware context is the foundation for high‑precision analytics, high‑recall automation, and efficient investigations across your environment.

Multi-Method Threat Detection
To ensure threats don't slip through cracks, we employ multiple methods of detection.
To ensure threats don’t slip through the cracks, our platform applies multiple analytic techniques to automatically detect both known and novel (zero‑day) attacks across endpoint, identity, and network.
Threat hunting is accelerated by RADICL Query Language (RQL), which lets analysts and AI hunt in entity context for faster, more accurate decisions. By automating correlation and triage across all these signals, RADICL delivers broader, deeper coverage than typical SMB solutions, without the enterprise‑grade price tag.

Case Management and Audit-Ready Evidence
Trusted Operations Require Tracking of Risk and Work
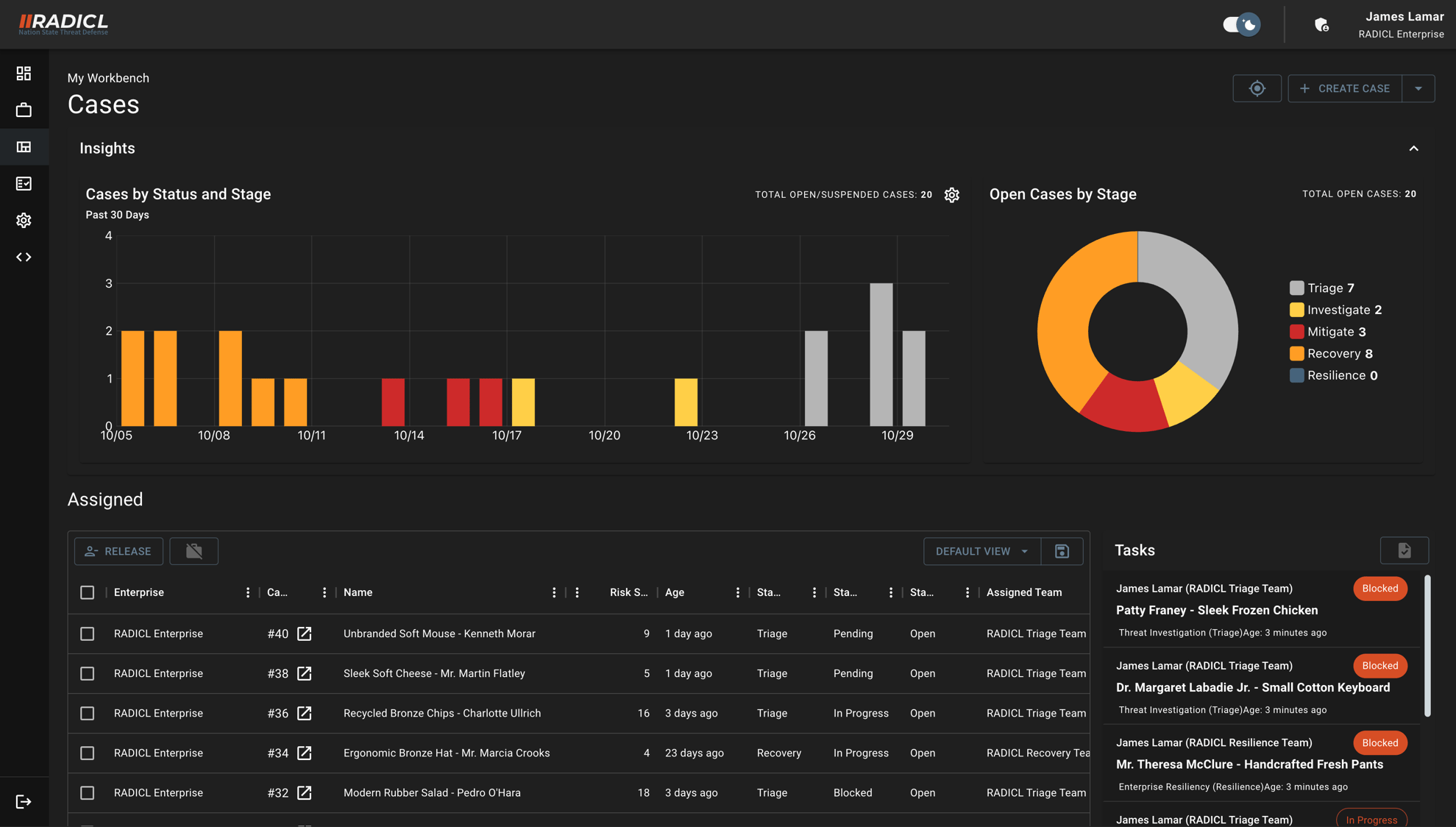
Our embedded Case Management ensures all threat indicators and incidents are tracked to completion. All workflows are designed to optimize analyst speed and accuracy, with ever-increasing application of AI-augmented automation.
All activity and evidence are fully tracked for full transparency and collaboration across RADICL analysts and protected clients, creating audit‑friendly evidence you can use for CMMC/NIST readiness.
Managed Security Operations Workflow
When work is required of you, we tee it up with expert guidance.
Embedded in the RADICL Platform is a purpose‑built project and task management system for managed security operations.
Work management allows us to consistently define, drive, and track the work that must be performed by us and by our protected clients.
Intelligent routing assigns tasks to the right owner: RADICL, your team, or your MSP, so remediation is completed quickly and consistently. By automating this operational overhead, RADICL delivers the discipline of an enterprise SOC while keeping service costs aligned to SMB budgets.

Enterprise Visibility and Collaboration with Dashboards
Trusted protection requires transparency and fast collaboration.

Real‑time dashboards show active investigations, actions we’re taking on your behalf, and what’s needed from you. Collaboration features leverage your institutional knowledge to accelerate decision‑making and improve outcomes.
Client visibility into active incidents and investigations is crucial to ensuring protection and trust. Our real‑time dashboards show active investigations, actions we’re taking on your behalf, and what’s needed from you. Collaboration features leverage your institutional knowledge to accelerate decision‑making and improve outcomes.
Deep-Spectrum Protection
See How Protection Stacks in Practice

Ransomware
Endpoint Detection and Response blocks initial access. 24/7 monitoring detects encryption activity within minutes. Network isolation prevents lateral movement. Managed Attack Surface eliminates exploitable vulnerabilities.

Phishing/BEC
Continuous simulations with corrective training. Identity monitoring detects credential abuse and account takeovers. Endpoint catches malicious activity when phishing succeeds.

Data Theft
Detects abnormal file access and exfiltration attempts. Identifies compromised credentials accessing sensitive data. Weekly hunts uncover low-and-slow theft operations.

Financial Fraud
Detects account takeovers targeting financial systems. Custom analytics identify invoice manipulation and fraudulent transactions. Behavioral monitoring flags unusual access.

APTs
Weekly Deep Spectrum hunts find embedded threats. Custom analytics detect living-off-the-land techniques. Cross-infrastructure correlation connects subtle indicators.

Compliance Failure
Weekly expert consultations with spot-checked evidence. Direct coverage of 29 CMMC controls. Platform-consolidated documentation. Quarterly reviews catch drift before audits.
Ready to Modernize Security Operations?
Launch a 24/7 vSOC in 7 days. Unify detection, response, vulnerability reduction, and CMMC/NIST compliance, with verified remediation and audit-ready evidence built in.
Frequently Asked Questions
What is a security operations platform?
A security operations platform centralizes threat detection, incident response, vulnerability management, and compliance operations into unified workflows. RADICL delivers Cybersecurity-as-a-Service (CSaaS), combining AI-powered security analytics with expert human analysts to provide enterprise-grade security operations as a managed service—technology, expertise, and 24/7 operations in one subscription.
How is the RADICL platform different from SIEM or XDR alone?
Traditional SIEM and XDR require constant tuning, health monitoring, and dedicated staff to operate effectively. Most SMBs lack the capacity to maintain these platforms while also conducting threat hunts, managing incidents, and driving remediation workflows. RADICL provides Managed Detection and Response with the operations team included. We handle deployment, custom detection analytics, weekly threat hunts, end-to-end incident management, and verified vulnerability remediation. You get complete security operations, not just expensive tools.
How fast can we deploy?
Most customers are fully operational within a week. EDR sensors and identity integrations get connected quickly. Custom detection analytics tune to your environment as we establish baseline visibility. Our threat hunting service and incident response platform capabilities go live while compliance assessment and remediation planning ramp up in parallel. Unlike traditional security projects that drag on for months, RADICL's platform-enabled approach delivers immediate protection.
How do you work with our MSP and existing tools?
RADICL integrates with your existing EDR, identity platforms, firewalls, and ticketing systems. We coordinate remediation through secure platform workflows. When your MSP needs to act, we provide detailed tasks with step-by-step instructions and track completion. Your MSP handles infrastructure while we provide specialized security expertise through our Security Operations Center as a Service model. No vendor competition, just coordinated protection.
How do you verify remediation and retain audit evidence?
Every remediation task includes closed-loop verification. For vulnerabilities, we rescan to confirm patches are applied. For incidents, we validate containment through forensic review using our incident response platform. For compliance, our consultants spot-check evidence before audits. All documentation, evidence, and verification records are consolidated in the platform with auditor access—eliminating the scramble to gather proof during assessments.
How does RADICL support CMMC and NIST 800-171 (SPRS)?
RADICL's MDR-as-a-Service, Managed Attack Surface, and Managed Security Awareness services directly satisfy 29 CMMC Level 2 controls. Our Managed Compliance Adherence service guides weekly self-assessments for remaining requirements with expert remediation instructions and audit-ready evidence collection. The platform maintains accurate SPRS scoring through continuous control monitoring. Compliance reviews catch control drift before audits, and our consultants prepare you for C3PAO assessments with spot-checked evidence and consolidated documentation.















