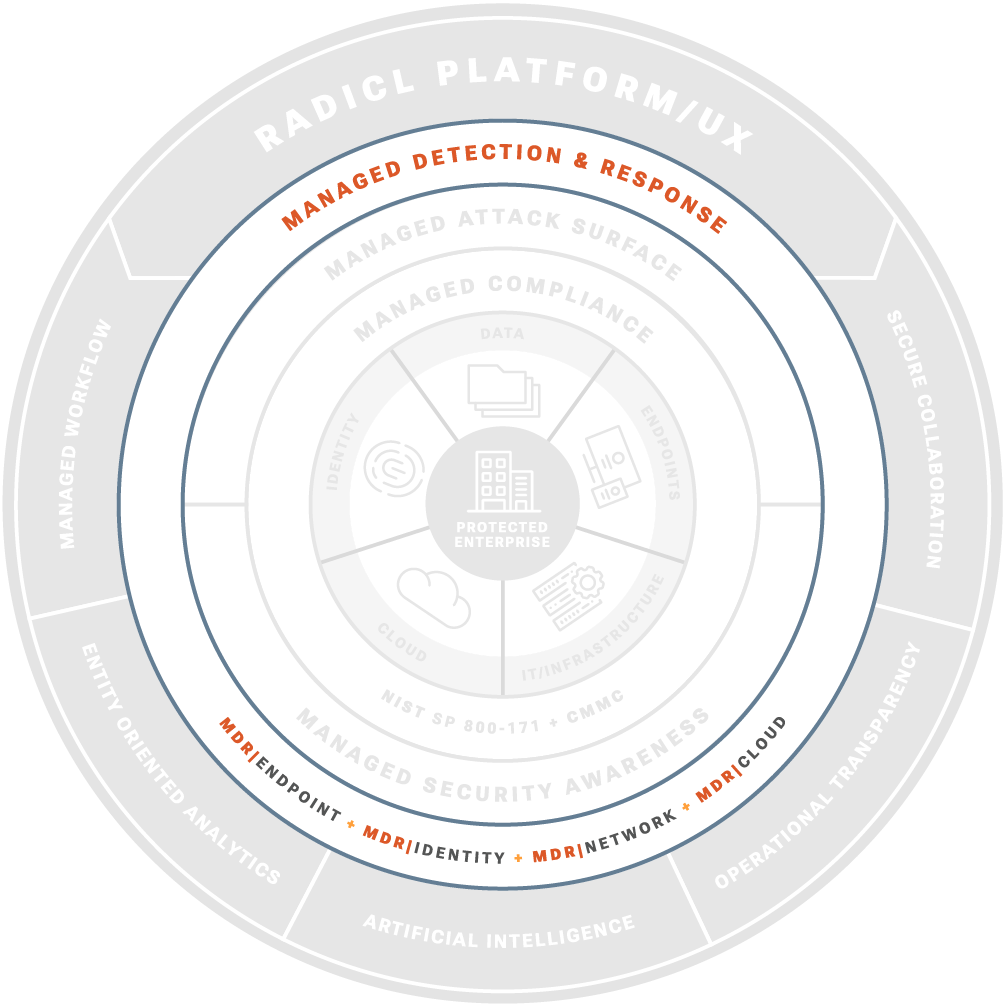
MANAGED DETECTION & RESPONSE
How Our Managed Detection and Response (MDR) Service Works
Our MDR services combine endpoint protection, threat hunting, and a 24x7 security operations platform, giving defense contractors a proven managed detection and response solution that closes gaps other MDR providers and vendors miss.
Endpoints Protected with MDR Security
We’ll deploy and manage leading endpoint threat detection and protection technology, ensuring user devices and servers are safe from attack to help maintain NIST 800-171 and CMMC Compliance.
Evasive & Embedded Threats Detected
We’ll execute military-grade threat hunting to search for advanced threats already present in the environment. We run continuous threat analytics to ensure indicators of new threats are immediately detected, supported by our integrated Managed Attack Surface visibility.
24 x 7 Security Operations Has Your Back
The RADICL vSOC Team is operating 24 x 7 on your behalf, ready to respond, investigate, and kill threats before damage is done.
Incidents Managed End-to-End
Our vSOC doesn’t just pass alarms back to your team. We orchestrate the full incident response process, coordinating actions across endpoints, identity, and network.
Virtual CISO By Your Side
If a major incident occurs (e.g., ransomware), we will serve as your virtual Chief Information Security Officer (CISO) ensuring senior leadership has expertise and guidance by their side. Paired with our Managed Security Awareness program, this helps strengthen your people, process, and technology defenses.
Our MDR Solutions & Services
RADICL provides three distinct MDR offerings to ensure no blind spots exist.
Your journey can start by focusing on endpoint protection, detection and response. Or you can start with all three, ensuring comprehensive protection day one.
MDR | Endpoint
The foundation of our MDR offering is MDR | Endpoint. We partner with industry leading EDR technologies like CrowdStrike and SentinelOne to ensure the strongest protection and visibility possible.
These leading technologies provide comprehensive detection and prevention of known threats. RADICL's custom detection analytics provide additional coverage along with 24/7 vSOC analysis of suspicious activity.
- EDR deployment: We expertly deploy, optimize, and maintain the EDR technology across in your environment.
- Comprehensive endpoint coverage: Protection spans laptops, workstations, physical servers, and virtual/cloud servers.
- Threat detection and prevention: EDR identifies and blocks a wide variety of known attacks across endpoints.
- Suspicious activity analysis: When unusual behaviors are detected, the RADICL vSOC investigates further to determine if they represent a potential security incident.
MDR | Identity
With MDR | Identity, we collect data from Microsoft O365 or Google Workspace and analyze user activity across the environment. This includes authentication attempts, file and data access, and email activity. One of the first things threat actors do when they compromise an environment is gain access to legitimate user credentials, allowing them to impersonate employees and burrow deeper into IT infrastructure. MDR | Identity is an essential layer of defense to ensure identities are secured and attackers are stopped before they can operate undetected.
- Authentication monitoring: Analyze authentication activity to detect unusual patterns that may indicate account compromise.
- Data and file access visibility: Track activity around sensitive files and email to identify potential data and inbox compromise.
- Credential misuse detection: Monitor for attackers impersonating legitimate users and attempting to escalate privileges within the environment.
- Custom detection analytics: Deploy custom analytics to detect indicators of account, data, and inbox compromise unique to your environment.
MDR | Network
With MDR | Network, we collect alarm and threat data from network security devices such as firewalls, threat management platforms, and intrusion detection systems. These tools provide visibility into external, network-borne threats as well as suspicious activity within IT and cloud environments. When alarms or threat indicators are raised, the RADICL vSOC investigates them thoroughly, leveraging visibility from MDR | Endpoint and MDR | Identity to provide a complete view.
- Comprehensive data collection: We collect alarms and threat data from firewalls, intrusion detection, and threat management systems.
- Visibility into network-borne threats: Detects suspicious interactions between internal and external systems, including activity inside cloud environments.
- Integrated investigations: The RADICL vSOC combines insights from MDR | Endpoint and MDR | Identity to analyze and resolve network alerts.
- Layered defense approach: MDR | Network provides an additional layer of visibility to ensure every potential threat is detected and investigated.
Most DIB SMBs Lack the Speed to Detect and Stop Advanced Attacks
Too many defense contractors can’t spot intruders until it’s too late, and even when they do, response times are measured in days. Meanwhile, account takeovers and endpoint compromises are happening at scale.
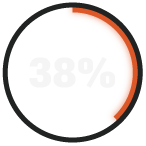
would take a week or more to detect a threat in their environment.
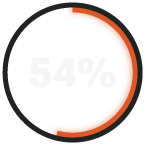
say it would take two days or longer to fully respond to ransomware or a breach.
Managed Detection & Response is built to close these gaps. With advanced endpoint protection, continuous threat hunting, and 24x7 incident response, RADICL ensures threats are found fast and stopped before they spread, while Managed CMMC Compliance keeps those response workflows aligned with NIST 800-171 and CMMC Level 2 requirements.
Get the Visibility You Deserve
At RADICL, operational transparency is a core value. We want you to know exactly what we are doing to keep you secure and compliant. As a customer, you should demand no less from a managed security services provider. Through transparency comes accountability and trust.
RADICL's Protection Delivered Dashboard
Watch this video to learn how with RADICL, you'll enjoy real-time visibility into how we are:
Frequently Asked Questions
How does RADICL MDR help with CMMC and NIST 800-171 compliance?
RADICL's managed detection and response services directly satisfy 29 of the most complex and costly CMMC Level 2 requirements across 10 domains including audit logging, threat monitoring, incident response, and vulnerability management. Our 24x7 security operations platform centralizes evidence collection, maintains continuous compliance posture, and provides audit-ready documentation. Whether you're pursuing CMMC certification or maintaining NIST 800-171 adherence, RADICL becomes your compliance operations team—driving assessments, remediations, and readiness without adding headcount. Learn more about our Managed CMMC Compliance Adherence solution.
What makes RADICL MDR different from other MDR providers or vendors?
Unlike traditional managed detection and response providers, RADICL delivers end-to-end incident ownership, not just monitoring and alerts. As a comprehensive MDR security company, we harden organizations, hunt embedded threats using Deep Spectrum methodologies, and manage the complete response lifecycle. Our MDR platform powered by digital agents working alongside human operators provides continuous hunting across endpoint, identity, and network, eliminating blind spots. Where legacy MSSPs forward alerts and narrow MDR vendors focus on single domains, RADICL's managed threat detection and response solutions seamlessly become your security operations team with absolute transparency and comprehensive coverage purpose-built for SMBs in the Defense Industrial Base.
Do I need all three MDR solutions (Endpoint, Identity, Network), or can I start with one?
You can start with any managed detection and response services module based on immediate priorities, many DIB contractors begin with Endpoint MDR for foundational protection. However, advanced threat actors move laterally across domains. Comprehensive protection requires visibility everywhere adversaries operate: endpoints where malware executes, identities attackers compromise, and networks they traverse. RADICL's modular MDR solutions let you land with one capability and expand as threats evolve and compliance requirements grow. Pair MDR with our Managed Attack Surface and Managed Security Awareness offerings for complete defense-in-depth.
How fast can RADICL detect and respond compared to other MDR services?
RADICL's virtual security operations center monitors alerts 24/7 and triages high-risk indicators within minutes, not hours or days. Our survey data shows 38% of DIB SMBs take a week or more just to detect threats, and 54% need two days or longer to respond to ransomware. Among managed detection and response providers, RADICL compresses these timelines dramatically through AI-accelerated detection, continuous threat hunting, and autonomous response capabilities built into our MDR platform. When every minute counts against nation-state adversaries, RADICL's speed advantage prevents minor incidents from becoming catastrophic breaches.
How does RADICL MDR integrate with our existing IT and compliance tools?
RADICL's MDR solutions integrate seamlessly with your existing infrastructure—MSPs, cloud platforms, identity providers like Entra ID, and endpoint solutions including CrowdStrike, SentinelOne, and Microsoft Defender. Our managed threat detection and response platform collects and correlates data across your entire IT environment without requiring you to rip and replace current investments. For compliance, RADICL works alongside your GRC tools to centralize evidence, track remediations, and maintain audit readiness for CMMC and NIST 800-171. The result: enhanced protection without operational disruption, what sets leading MDR vendors apart.














