BEYOND THE BASIC SOC
Harden - Detect - Respond - Comply
Traditional SOCs Can't Keep Pace With Modern Threats
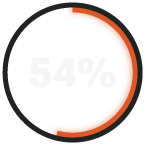
of defense contractors take 2+ days to respond to a breach
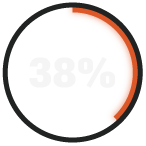
need a week just to detect a threat in their environment
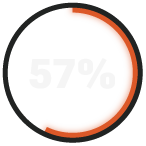
report their threat hunting is barely effective
The gap isn't technology—it's operational capacity.
AI-only SOCs miss critical context. Human-only SOCs can't scale. MSSPs monitor and forward alerts, leaving you to respond alone.
RADICL vSOC delivers both: Digital agents for velocity and scale. Human operators for judgment and expertise. Complete ownership from detection through resolution.
What Our vSOC Does

COMPLIANCE OPERATIONS
- Self-Assessments
Drive and guide periodic assessments to identify gaps before audits do. - Gap Remediations
Develop and track remediation actions with expert guidance. - Audit Preparation
Ensure evidence of compliance is gathered, organized, and audit-ready.
HARDEN OPERATIONS
- Endpoint Protection
Deploy and manage advanced EDR technology on servers and workstations. - Security Awareness Training
Educate employees and test resilience against phishing and social engineering. - Vulnerability Management
Identify, prioritize, and remediate vulnerabilities to minimize exploitable weaknesses.
DETECT OPERATIONS
- Visibility
Centralized log collection and processing across your entire security and IT enviornment - Detection Analytics
Advanced rules and anomaly detection to identify threats across the attack lifecycle. - Threat Hunting
Embedded Threat Hunts to find adversaries that have already made their way in. Continuous analytics for real-time detection.
RESPOND OPERATIONS
- 24/7 Monitoring
Round-the-clock evaluation of high-risk indicators. Minutes to triage, not hours. - Threat Investigation
Forensic analysis and log review to determine scope, impact, and root cause. - Incident Response
Rapid containment, comprehensive response plans, and stakeholder communication management.
What Makes RADICL vSOC Different
We Deliver Compliance Operations—Not Just Technology
RADICL meets 29 CMMC Level 2 controls out of the box—and helps you close the rest.
- Automated readiness assessments
- Expert-guided remediation workflows
- Continuous evidence collection
Audit-ready. Effort-light. Always compliant.
We Harden Organizations—Not Just Monitor Them
Traditional SOCs wait for alerts. RADICL reduces your attack surface before threats appear.
- Continuous vulnerability management
- Phishing simulations & awareness training
- Endpoint protection + MSP accountability
Smaller surface. Fewer breaches. Proactive defense.
We Hunt Deep—Not Just Surface-Level
Deep Spectrum Hunting uncovers stealthy, long-lived threats others miss.
- Endpoint, identity, and network visibility
- TTP-based hunting, not just IOCs
- Continuous analytics + scheduled deep hunts
Hidden threats exposed.
We Own Incidents—Not Just Forward Alerts
End-to-end response from detection through recovery.
- Full triage, investigation, and containment
- Project-managed IR
- In-house forensics expertise
No alerts dumped in your lap. Ever.
Human + AI Operations—Velocity Meets Accuracy
Digital agents analyze and correlate threats in real time. Human experts investigate, respond, and learn from every event.
Minutes to detection. Zero alert fatigue. Smarter defense daily.
Digital Agents + Human Operators + Your Team
Seamless team extension, not vendor management.
How Fast Do We Respond?
While 54% of organizations take 2+ days to respond to a ransomware attack, RADICL vSOC operates on a different timeline:

Minutes to triage
Digital agents analyze every alert in real time. Human operators assess priority threats within minutes.

Hours to contain
When threats are confirmed, containment begins immediately—not after a ticket is filed.

Complete Resolution
Full investigation, remediation, and environment hardening—no partial handoffs, no closed tickets without closure.
What Threats Does the vSOC Detect?
Ransomware
Phishing & Account Takeover
Endpoint Compromise
Insider Threats
User behavior analytics to identify data exfiltration, policy violations, and malicious activity.
Network Intrusions
Traffic analysis for command-and-control communications, lateral movement, and data staging.
Supply Chain Attacks
Third-party access monitoring and software supply chain integrity validation.
See how digital agents and human operators work together to protect your environment.
See our Threat Hunters in action fighting the most advanced nation state threat actors.
Questions about your specific environment? Let's talk.
Frequently Asked Questions
MSSPs monitor your environment and send you alerts. RADICL vSOC owns the complete incident lifecycle—detection, investigation, containment, response, and remediation. We don't hand you a ticket. We hand you a resolved incident.
We can take over as your complete SOC, work alongside your existing team to handle specific operations, or augment your analysts by taking tier-1 and tier-2 work off their plate. You choose the model that fits your organization.
Most customers are fully onboarded in 7 days. We deploy endpoint agents, configure log collection, establish baselines, and begin 24/7 monitoring within a week.
CMMC Level 2, NIST SP 800-171, NIST CSF, PCI DSS, HIPAA, and more. Our Comply Operations module guides you through any framework your business requires.
The RADICL platform gives you complete visibility into all operations—cases, tasks, remediations, hunts, and investigations. You see everything we do in real-time.
We respond immediately. Containment actions happen in minutes, not morning. We'll brief your team when appropriate, but we don't wait for business hours to protect your environment.
Standalone tools like EDR and SIEM are the building blocks of defense in depth, but they only deliver value when a skilled team manages them day to day. Cybersecurity-as-a-Service (CSaaS) providers go further by combining expert operations with their own proprietary technology stack, delivering a fully managed threat detection and response solution. Instead of leaving SMBs to juggle multiple tools and platforms, CSaaS provides continuous threat hunting and monitoring out of the box. At RADICL, we also support side-by-side operations, giving customers access to the same platform and toolset our analysts use, creating a best-of-both-worlds model that builds true cyber resilience.
Stop Managing Vendors. Start Operating With a Real Security Team.
See how RADICL vSOC becomes your security and compliance operations team.
















