Managed Cybersecurity Services
WE PROTECT AMERICAN SMBs FROM ADVANCED CYBERTHREATS
SMBs of high interest to cybercriminals and nation state threats deserve "military-grade" defense-in-depth protection.
Fully Managed Cybersecurity-as-a-Service for Regulated Industry SMBs
RADICL acts as your dedicated security operations team and compliance partner. We deliver continuous monitoring, incident response, and compliance reporting as a single, fully managed cybersecurity‑as‑a‑service offering.
Battle-tested, proven, and trusted by companies who demand the best.
SMBs Deserve Better
Basic IT security controls and generic MSP services aren't enough to keep regulated industry SMBs and other high‑value American businesses secure or compliance-ready (e.g. CMMC).

You're a growing target for cyber attacks
SMBs with sensitive data, IP, or federal contracts are increasingly targeted by cybercriminals and nation‑state actors. RADICL helps you defend against enterprise threats.

Enterprise solutions aren't built for you
Enterprise platforms assume you have a SOC to run them, but most SMBs don’t. RADICL delivers a managed, AI‑assisted platform and vSOC focused on outcomes, not dashboards.

Basic security isn't enough anymore
Firewalls and antivirus aren’t defense‑in‑depth. RADICL closes gaps across endpoints, identity, networks, and your external attack surface, before they become incidents.

Most service providers overlook SMBs entirely
Many vendors price SMBs out or treat them as an afterthought. RADICL is built for SMBs, combining AI workflows with a dedicated vSOC for enterprise‑level protection.

Full Security Operations in 7 Days
Stand up CMMC‑ready security operations in as little as 7 days. RADICL deploys your vSOC, endpoint protection, and core monitoring fast—without hiring an internal team.

Complete Visibility
Get real‑time visibility across your environment and alignment to frameworks like CMMC. See alerts, investigations, and remediation in one place.

True 24 / 7 Protection
RADICL’s vSOC monitors and responds 24/7. When threats appear, we respond in minutes and coordinate remediation with your IT or MSP to keep operations and contracts on track.

Advanced Threat Hunting
Threat hunting that detects silent, evasive activity other tools (and typical MDRs) miss. Stay ahead of sophisticated adversaries targeting sensitive data.

Cost-Effective Security Operations
Get the vSOC team, platform, and CMMC‑aligned operations for a predictable monthly fee, without the overhead of building a SOC.

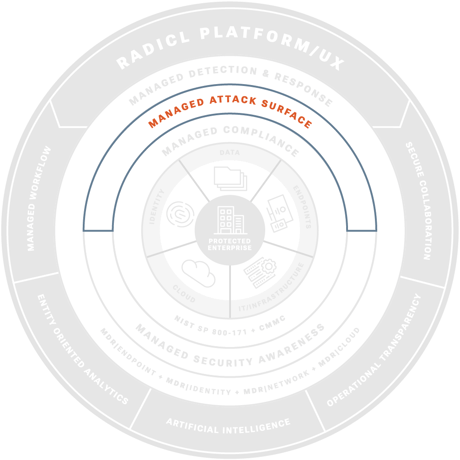
Defense-in-Depth, Powered by AI
Layer MDR, identity/email monitoring, network visibility, attack surface reduction, security awareness, and compliance adherence. AI helps our analysts move faster so advanced threats slip through less often.
RADICL Becomes Your Security Operations Team
— Quickly and Seamlessly —
Our Virtual Security Operations Center (vSOC), powered by our proprietary RADICL Platform quickly and seamlessly becomes your security operations team. From onboarding to day-to-day activities, RADICL Platform is designed to be transparent, collaborative, and easy for busy SMB leaders and IT teams to work with.

Our vSOC is staffed with cybersecurity and compliance experts who apply their experience and knowledge, combined with the strengths of our platform, to keep you secure, compliant, and audit-ready.
The RADICL Path to Strong Security
Comprehensive protection and turn-key service powered by an agentic, autonomous vSOC. The RADICL Platform delivers enterprise-grade security and compliance operations for SMBs, keeping you highly secure and contract-ready without adding complexity.


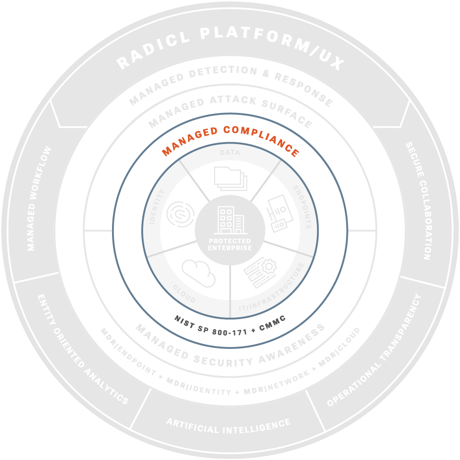
Drive Cybersecurity Compliance & Best Practices
Compliance requirements guide security operations aligned to CMMC, NIST 800-171, and industry frameworks.

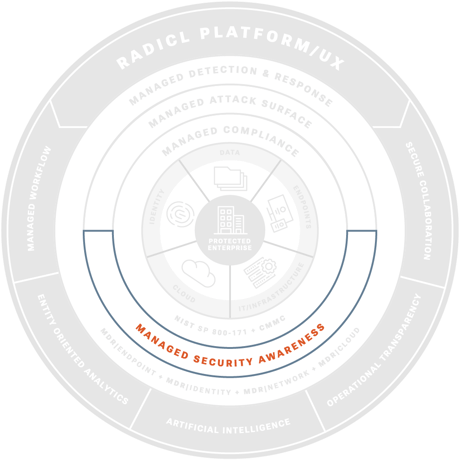
Reduce IT and Human Vulnerability
Close security gaps through awareness training, patching, and configuration hardening.

Protect Endpoint / Server / Cloud Infrastructure
Secure devices, workloads, and cloud environments with unified visibility and control.

Hunt for Threats, Deep & Emergent
Deep threat hunts uncover embedded adversaries while continuous analytics catch emerging threats in real time.

Monitor, Triage, & Respond Incidents 24/7
No blame game. We detect, investigate, and contain threats around the clock with expert SOC analysts.
Our Solutions
Managed Detection and Response
|
Advanced endpoint protection, military-grade threat hunting, and 24×7 incident response ensure your company is safe from ransomware, data theft, financial fraud, and other high-impact cyber risks while supporting compliance requirements like CMMC and NIST 800‑171.
Endpoints and Servers Protected
Evasive & Embedded Threats Detected and Stopped
24×7 Security Operations Has Your Back
Incidents Managed End-to-End
Virtual CISO By Your Side
|
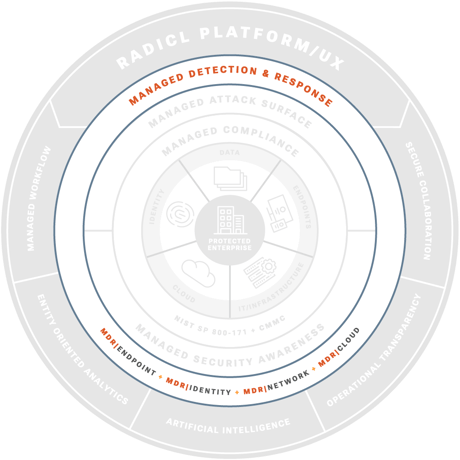 |
MDR | Endpoint
MDR | Identity
MDR | Network
Managed Attack Surface
Managed Security Awareness
Managed Compliance Adherence
What RADICL Protects You From
Advanced persistent threats (APTs) are well resourced adversaries with time and expertise who exploit organizations through ransomware, phishing, account compromise, data theft, financial fraud, and compliance gaps. The RADICL Platform delivers deep spectrum™ visibility and continuous threat hunting to detect intrusion patterns before they disrupt your business, customers, or compliance posture.

Ransomware
Ransomware halts production, exposes data, and triggers regulatory issues. RADICL detects early compromise signals, contains threats fast, and coordinates remediation with your IT/MSP.

Phishing/BEC
AI powered phishing impersonates trusted contacts. Someone will eventually click. RADICL combines security awareness training with monitoring that blocks malicious payloads and flags suspicious behavior.

Email & Account Compromise
Compromised accounts lead to BEC, data theft, and fraudulent payments. RADICL monitors Microsoft 365 and Google Workspace for unusual sign ins, risky inbox rules, and abnormal data movement. Our vSOC investigates, contains threats, and guides remediation.

Data Theft & Insider Risk
Data loss damages trust and creates compliance exposure. RADICL correlates endpoint, identity, and network signals to detect abnormal access and exfiltration from external attackers or manipulated insiders.

Financial Fraud
AI driven impersonation makes fraud harder to spot. RADICL trains employees, monitors for fraud precursors like anomalous payment requests, and provides 24×7 response to stop threats before funds move.

Compliance Failure
RADICL aligns security operations to CMMC, NIST 800‑171, and other frameworks. We close control gaps, maintain audit ready evidence, and provide real time risk visibility.
Cyber Resilience at the Crossroads
In this eye-opening discussion, three national security experts reveal how Chinese state actors have embedded malware throughout transportation, energy, and communications networks as part of a deliberate war-winning strategy.
The Majority of SMBs Are Unprepared to Deal With a Motivated Cyberthreat
For the second consecutive year, RADICL has polled IT and security leaders at SMBs serving the DIB and found that while there have been some improvements, the results are still cause for concern, with most companies remaining unprepared to protect against sophisticated cyber threats.
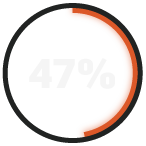
had four or more user accounts or emails compromised in the past year.
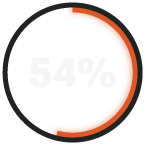
say it would take two days or longer to respond to ransomware or a breach.
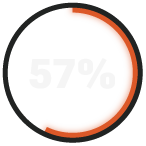
report low to medium effectiveness in threat hunting.
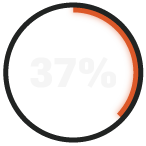
say cybersecurity-related incidents have cost their company $100,001.
What Our Customers Are Saying



RADICL Has Been Featured In:





Frequently Asked Questions
What makes RADICL different from an MSP or typical MDR provider?
MSPs monitor and forward alerts while MDRs detect but don't remediate. RADICL delivers complete incident ownership—we detect, investigate, respond, and manage remediation through our virtual SOC, becoming your security and compliance team.
Can RADICL help us get ready for CMMC and NIST 800-171?
As a CMMC compliance company, RADICL's managed security operations directly address some of the most challenging Level 2 controls. Our CMMC as a service model delivers platform-driven self-assessments, expert remediation guidance, and audit-ready evidence collection.
How quickly can RADICL get us protected and on a CMMC compliance path?
Protection starts within 7 days with full monitoring across endpoints, identities, and networks. Our CMMC compliance solutions automatically addresses requirements on day one, we then guide weekly milestones to close remaining gaps.
Will RADICL replace our MSP or internal IT team?
No—RADICL complements your team by handling security and compliance operations while your MSP or IT focuses on productivity and infrastructure. Think of us as the cybersecurity defense contractors expertise you couldn't afford to hire, working alongside your existing resources.
What does RADICL actually take off my plate day-to-day?
We handle 24/7 monitoring, threat investigation, weekly threat hunting, vulnerability management, security awareness training, and ongoing compliance operations. You get transparent visibility and executive briefings while the operational burden moves entirely to our virtual SOC.
Does RADICL integrate with our existing MDR, EDR, and security tools?
RADICL includes best-in-class EDR and integrates with your identity providers, cloud platforms, and network infrastructure for comprehensive visibility. Our CMMC software consolidates separate MDR, MSSP, and vulnerability scanning capabilities while reducing vendor complexity.
What happens during a security incident when RADICL is my vSOC?
We own it from detection through resolution—triage within minutes, investigate scope, contain threats immediately, and coordinate all remediation. You're informed at every step, but technical investigation and response execution are entirely handled by our incident response team.
Is RADICL built only for DIB contractors, or can other high-risk SMBs use it too?
RADICL was purpose-built for cyber security defense contractors, giving us unmatched CMMC and NIST 800-171 expertise. Any SMB in regulated industries—healthcare, financial services, or critical infrastructure—benefits from the same enterprise-grade protection without enterprise complexity.