Defending American SMBs From Advanced Cyberthreats
Defense-in-depth against nation-state threats, powered by 24/7 MDR with advanced detection, managed compliance, and Human + AI threat hunting.
Talk to Our Team!
Fully Managed Cybersecurity-as-a-Service
Human expertise powered by our technology. Battle-tested, proven and trusted by leading American SMBs and defense contractors.
The Majority of SMBs Are Unprepared to Deal With a Motivated Cyberthreat
For the second consecutive year, RADICL has polled IT and security leaders at SMBs serving the DIB and found that while there have been some improvements, the results are still cause for concern, with most companies remaining unprepared to protect against sophisticated cyber threats.
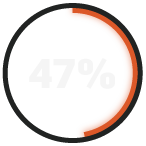
had four or more user accounts or emails compromised in the past year.
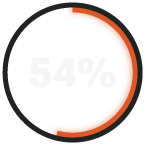
say it would take two days or longer to respond to ransomware or a breach.
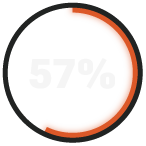
report low to medium effectiveness in threat hunting.
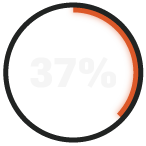
say cybersecurity-related incidents have cost their company $100,001.
SMBs Deserve Better
Basic IT security controls aren't enough and leave gaps. Small and mid-sized businesses need to adopt a defense-in-depth strategy to reduce their cybersecurity incident risk.

You're a growing target for cyber attacks

Enterprise solutions aren't built for you

Basic security isn't enough anymore

Most service providers overlook SMBs entirely

Full Security Operations in 7 Days
Get enterprise-grade protection without building an internal team. We handle everything from monitoring to compliance.

Complete Visibility
Real-time dashboard shows exactly what we're doing to protect your business. No more security black boxes.

True 24 / 7 Protection
Our virtual Security Operations Center (vSOC) provides round-the-clock monitoring, detection, and rapid response capabilities.

Advanced Threat Hunting
Military-grade threat hunting operations that find sophisticated attacks other tools miss. Built on defense industry expertise.

Cost-Effective Security Operations
Get the security team and technology you need without the overhead of building it yourself. One predictable monthly fee.
The RADICL Path to Stronger Security
Our mission is to keep you highly secure while keeping it easy for you.
Initial Consultation
We honestly evaluate your current security needs and whether we can help.
7 Day Deployment
In 7 days, your vSOC is live, endpoints protected, 24/7 threat response ready.
Continuous Ops
Ongoing security posture improvements and compliance adherence.
— Quickly and Seamlessly —
Our Virtual Security Operations Center (vSOC), powered by our proprietary RADICL XTP Platform quickly and seamlessly becomes your security operations team. From onboarding to day-to-day activities, RADICL XTP has been designed to provide customers with a transparent, collaborative, and easy-to-use experience.
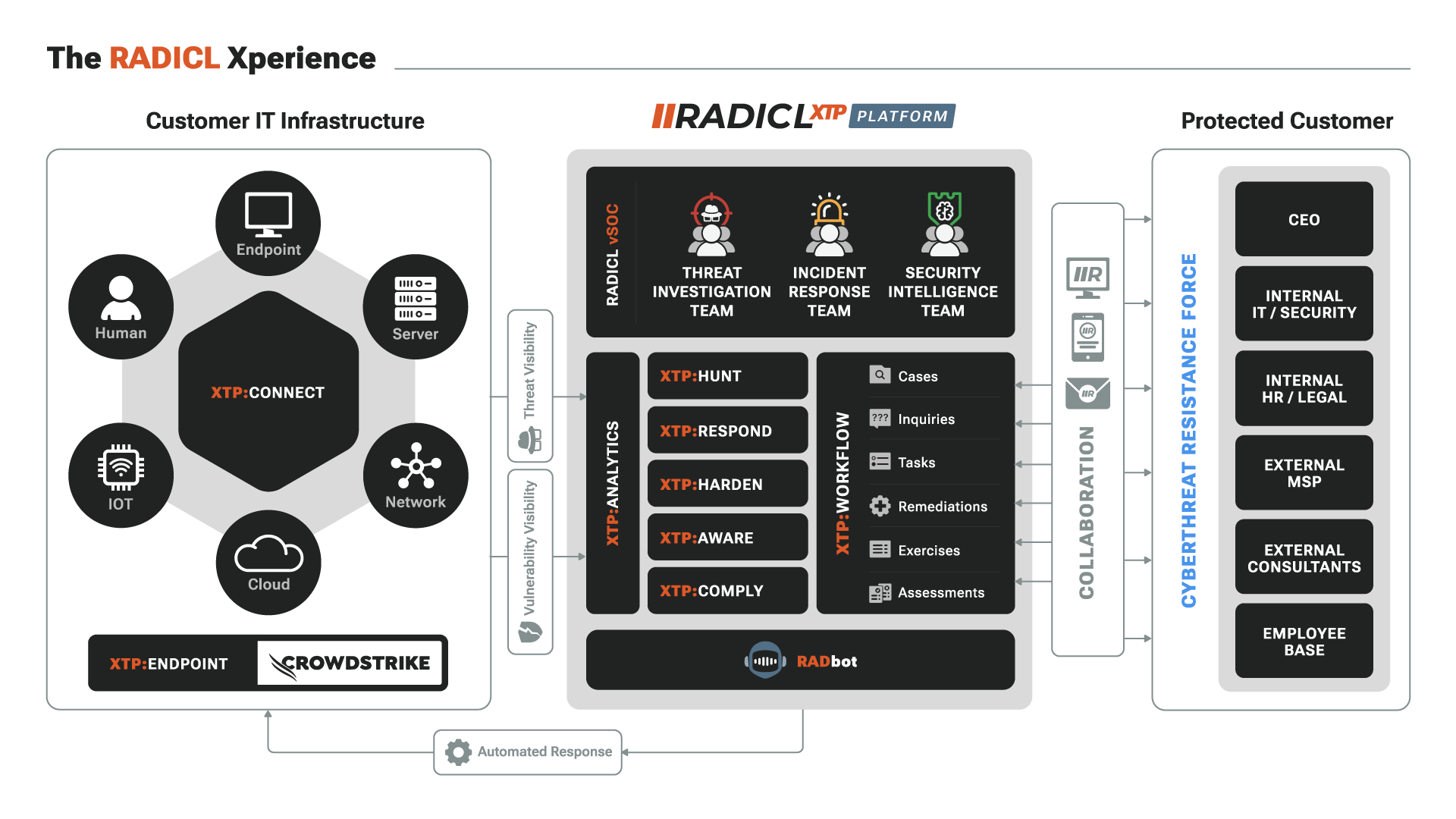
Our vSOC is staffed with cybersecurity and compliance experts who apply their experience and knowledge, combined with the strengths of our platform, to keep you secure and compliant.
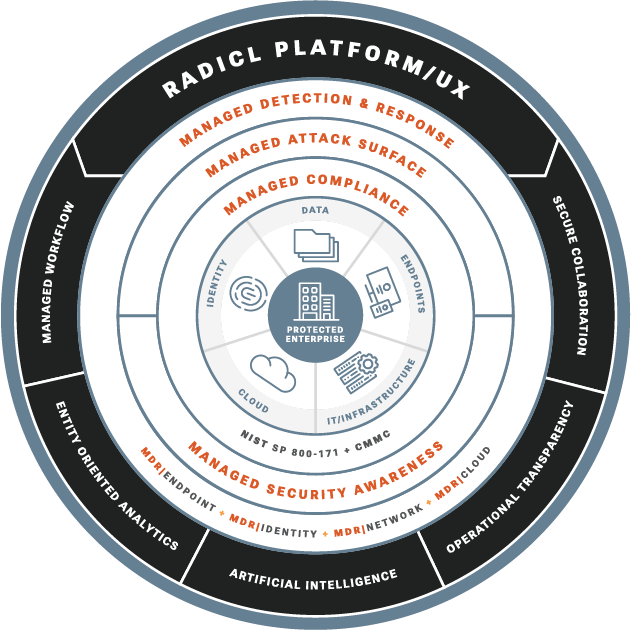
Our Solutions
Managed Detection & Response
|
Advanced endpoint protection, military-grade threat hunting, and 24x7 incident response ensure your company is safe from ransomware, data theft, financial fraud and other high impact cyber risks. Endpoints Protected
Evasive & Embedded Threats Detected
24 x 7 Security Operations Has Your Back
Incidents Managed End-to-End
Virtual CISO By Your Side
|
 |
Managed Attack Surface
|
Threat actors leverage vulnerabilities to get a foot in the door and expand their presence. Become a hard target. We'll persistently reduce your vulnerability exposure and risk. Endpoint and Server Vulnerabilities Detected
Pragmatic and Manageable Remediation Pace
Accelerated Critical Fix Response
Expert Guidance and Collaboration
Closed Loop "Fixed" Visibility
|
 |
Managed Security Awareness
|
People are too often the weak link. We'll shore up your human line of defense by ensuring employees can spot phishing attacks and their personal cybersecurity hygiene is strong. Comprehensive Annual Training
On-going "Bite Sized" Training
Phishing Attack Simulations
Ever Evolving Expert Content
Security Awareness Posture Visibility
|
 |
Managed Compliance Adherence
|
Compliance is a cost of doing business. It can cost less. We'll expertly guide and track your compliance journey, reducing confusion and cost along the way. Self-Assessments Guided and Made Easy
Adherence Gaps Quickly Closed
Audit Trail and Evidence Capture
Compliance Posture Clarity
External Audit Preparedness & Efficiency
|
 |
Cyber Resilience at the Crossroads
In this eye-opening discussion, three national security experts reveal how Chinese state actors have embedded malware throughout transportation, energy, and communications networks as part of a deliberate war-winning strategy.
What Our Customers Are Saying



RADICL Has Been Featured In





Frequently Asked Questions
MDR focuses on threat detection and response at the endpoint, but stops there—leaving you to coordinate incident response, manage compliance, and handle security operations. RADICL's Cybersecurity-as-a-Service (CSaaS) delivers complete security operations including MDR capabilities, managed compliance management, human led threat hunting, employee training, and infrastructure hardening. When an incident occurs, our vSOC doesn't just detect and alert, we contain, investigate, and fully resolve threats while managing all follow-up actions. Think of MDR as a security monitoring service; CSaaS is your complete virtual security team.
RADICL provides Managed Detection & Response with continuous monitoring from our U.S.-based vSOC. We combine automated detection with human operators to identify threats in real time, respond rapidly, and support your security and compliance requirements.
We include built-in compliance workflows, evidence collection, and reporting to help teams prepare for audits and maintain continuous compliance, including improvements to SPRS scoring and audit readiness.
Yes. RADICL is designed for SMBs in the Defense Industrial Base, delivering enterprise-grade protection without the need for a large internal security team.
We pair operations-led threat hunting and response with our platform and compliance capabilities, reducing detection and response windows and simplifying audit readiness.
Pricing is based on environment size and compliance scope. Book a demo to get a tailored quote.
Ready to Stop Managing Security and Start Running Your Business?
RADICL delivers enterprise-grade cybersecurity through AI-powered automation and human expertise — purpose-built for SMBs facing nation-state threats.














