Complete Enterprise Cybersecurity. Purpose-Built for SMBs
The SMB Reality
You're Facing Enterprise Threats on a Small Business Budget
Small and mid-sized businesses are prime targets for sophisticated attackers—but traditional security wasn't built for your reality. SMBs face critical gaps:
Enterprise Tech Stack Gap
Best-in-breed point tools and platforms across multiple threat vectors are expensive and difficult to configure and integrate. SIEM, EDR, XDR, threat intelligence platforms, SOAR, vulnerability management, and GRC tools—each is costly, together they're unattainable.
Expert Staffing Gap
Fully staffed SOCs require security analysts, threat hunters, and incident response specialists that SMBs struggle to hire and retain. 24/7 coverage requires teams of specialized experts at enterprise salary levels.
Service Provider Gap
Traditional MSSPs and MDRs fill some gaps but often just forward alerts and leave ownership gaps during critical incidents. During breaches, you become the project manager coordinating multiple vendors while adversaries move freely.
The Results
Fragmented solutions for overstressed teams that struggle to define vendor relationship boundaries. Enclave security that protects individual systems while advanced adversaries exploit the gaps.
From our 2025 DIB Report of 364 defense contractors:
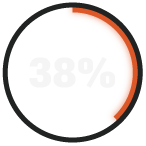
would take a week or more to detect threats in their environment
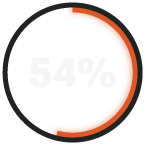
need 2+ days for full incident response
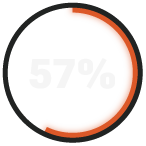
report only medium or low effectiveness in threat hunting
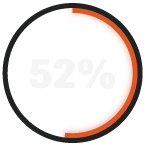
plan to switch security providers in the next year due to inconsistent service and limited compliance support
SMBs Need a Comprehensive and Cost-Effective Solution for Modern Cyberthreat Protection, Equally Equipped With Defense AI
Vertical, Best-in-Class Cyber Tech Stacks Unattainable for SMBs

Cyber Staff Rented From Low-Grade Managed Services
RADICL CSaaS: The Modern Solution
Purpose-Built, Integrated Cybersecurity-as-a-Service
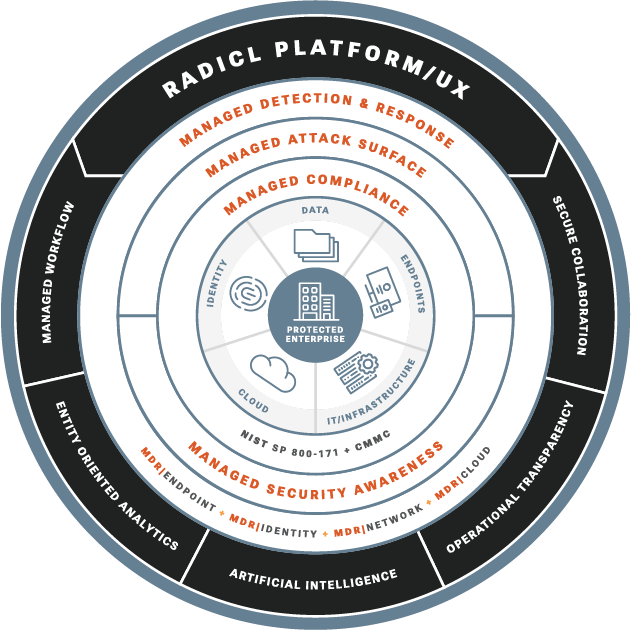
RADICL delivers a purpose-built, integrated CSaaS (cybersecurity-as-a-service) platform operated by digital agents and human experts, delivering Enterprise Security teams and tools to the SMB.
We seamlessly become your security and compliance operations team through the Radicl AI-native platform that powers a virtual Security Operations Center (vSOC) staffed in the USA 24/7.

COMPLIANCE OPERATIONSDrive Cybersecurity Compliance & Best Practices We ensure your organization adheres to cybersecurity frameworks and regulatory requirements through:
Audit-ready documentation and evidence collection from a CMMC RPO certified provider. |
 |
HARDEN OPERATIONSReduce IT and Human Vulnerability Proactive hardening reduces your attack surface and strengthens your security posture:
Continuous attack surface reduction through best-in-class tools managed protection and expert oversight. |
 |
DETECT OPERATIONSDeep Spectrum Threat Hunting Across Your Infrastructure Comprehensive threat detection across endpoints, network and identities:
Deep historical hunting plus real-time response catches threats others miss for months. |
 |
RESPOND OPERATIONSEnd-to-End Incident Response & Recovery When threats are detected, we own the complete response process:
Complete incident ownership from detection through recovery - no handoffs, no gaps. |
 |
Why Traditional Approaches Fail SMBs

The RADICL Advantage
Complete Service Ownership
- We become your security team, not another vendor
- End-to-end incident response, not ticket forwarding
- Transparency into all actions and operations
Organizational Hardening, Not Point Solutions
- We don't protect individual systems—we harden your entire organization
- Multi-domain visibility across endpoints, networks and identities
- No gaps for adversaries to exploit between tools or vendors
Deep Spectrum Hunting Methodology
- We find embedded threats other providers miss because we actually look
- Hypothesis-driven hunts across all security domains, not just automated alerts
- Embeeded Threat Hunting + Continuous Detection Analytics = Full domain threat hunting
AI-Powered Efficiency
- Digital agents accelerate detection, response, and remediation
- Human expertise where it matters most: hunting, investigation, response
- Enterprise-grade protection at SMB-affordable pricing
Defense-Focused Expertise
- Purpose-built for the Defense Industrial Base
- Deep understanding of CMMC, NIST SP 800-171, and federal requirements
- CMMC RPO certified with 29 Level 2 controls addressed turn-key
Frequently Asked Questions
Standalone tools like EDR and SIEM are the building blocks of defense in depth, but they only deliver value when a skilled team manages them day to day. Cybersecurity-as-a-Service (CSaaS) providers go further by combining expert operations with their own proprietary technology stack, delivering a fully managed threat detection and response solution. Instead of leaving SMBs to juggle multiple tools and platforms, CSaaS provides continuous threat hunting and monitoring out of the box. At RADICL, we also support side-by-side operations, giving customers access to the same platform and toolset our analysts use, creating a best-of-both-worlds model that builds true cyber resilience.
Cybersecurity for small businesses requires enterprise-level protection without enterprise complexity. RADICL delivers cybersecurity solutions for small business through an integrated cybersecurity management platform operated by AI and human experts. Unlike new cyber security companies offering point solutions or small cyber security companies with limited capabilities, we provide complete managed cybersecurity solutions that reduce complexity while enhancing security postures.
Yes - we integrate with MSPs and enhance their services by adding security expertise, compliance capabilities, and threat hunting that most MSPs lack. We hold your MSP accountable to cybersecurity best practices while filling critical gaps in detection and response.
We specialize in NIST Cybersecurity Framework (CSF), NIST SP 800-171 (all 110 requirements), CMMC Level 2, and other federal standards. Our cybersecurity management platform automates evidence collection and audit preparation, ensuring you're always audit-ready.
Our human centered cybersecurity approach uses AI-powered digital agents for speed and scale, while security experts handle critical decisions and complex investigations. This delivers executive cyber security visibility with operational depth - leadership gets clear risk communication while technical teams get expert-level threat hunting and incident response. It's the efficiency of automation with the judgment of experienced security professionals.
Ready to Stop Managing Security and Start Running Your Business?
RADICL delivers enterprise-grade cybersecurity through AI-powered automation and human expertise — purpose-built for SMBs facing nation-state threats.









