Defense in Depth Threat Hunting & Response
Defense contractors face nation-state actors and sophisticated eCrime groups targeting your CUI and IP. RADICL delivers proactive threat hunting and complete incident response across endpoints, identity and network - so you can focus on your mission instead of worrying about and responding to cybersecurity incidents.
Talk to Our Team!
24/7 U.S.-based Operations | Embedded Threat Hunts | Continuous Detection Analytics
Alerts Aren't Enough: You Need Proactive Detection
11 days — global median dwell time
Attackers remain undetected for nearly two weeks on average before discovery.
39% of breaches start with exploits
While everyone talks about phishing, attackers are still kicking down the front door through unpatched vulnerabilities.
43% of breaches are caught internally
The best-prepared organizations find threats themselves. Everyone else gets a phone call.
5 days — adversary notification time
Ransomware groups are efficient: they'll tell you about the breach faster than your own security team will.
RADICL's Defense in Depth Coverage
Real threats move across your entire infrastructure and operate on their own timelines. We hunt everywhere, all the time. Most MDR providers focus solely on endpoint detection, but sophisticated attackers like the Lazarus Group (APT38) operate across multiple domains to avoid detection:

Multi-Domain Coverage
Endpoint
Malicious scripts and backdoor installation
Network
Command-and-control communications and data exfiltration
Identity
Credential harvesting and privilege abuse
DeepSpectrum™ Threat Hunting
Embedded Threat Hunting
Discovers advanced persistent threats that have been operating undetected for weeks or months using living-off-the-land techniques.
Continuous Detection Analytics
Always on analytics providing multi-domain, 360 degree detection of threats across the entire IT infrastructure.
Why Both Matter: Emergent threats and APTs use novel attack methods that haven't been seen before. Once in they operate with stealth using live of the land techniques. Traditional MDR waits for signatures. RADICL hunts proactively for both established and emerging attack patterns - and we own the complete incident response when threats are found.
Why RADICL: Complete Threat Hunting & Response
We don't just find threats - we own the complete response from containment to recovery.
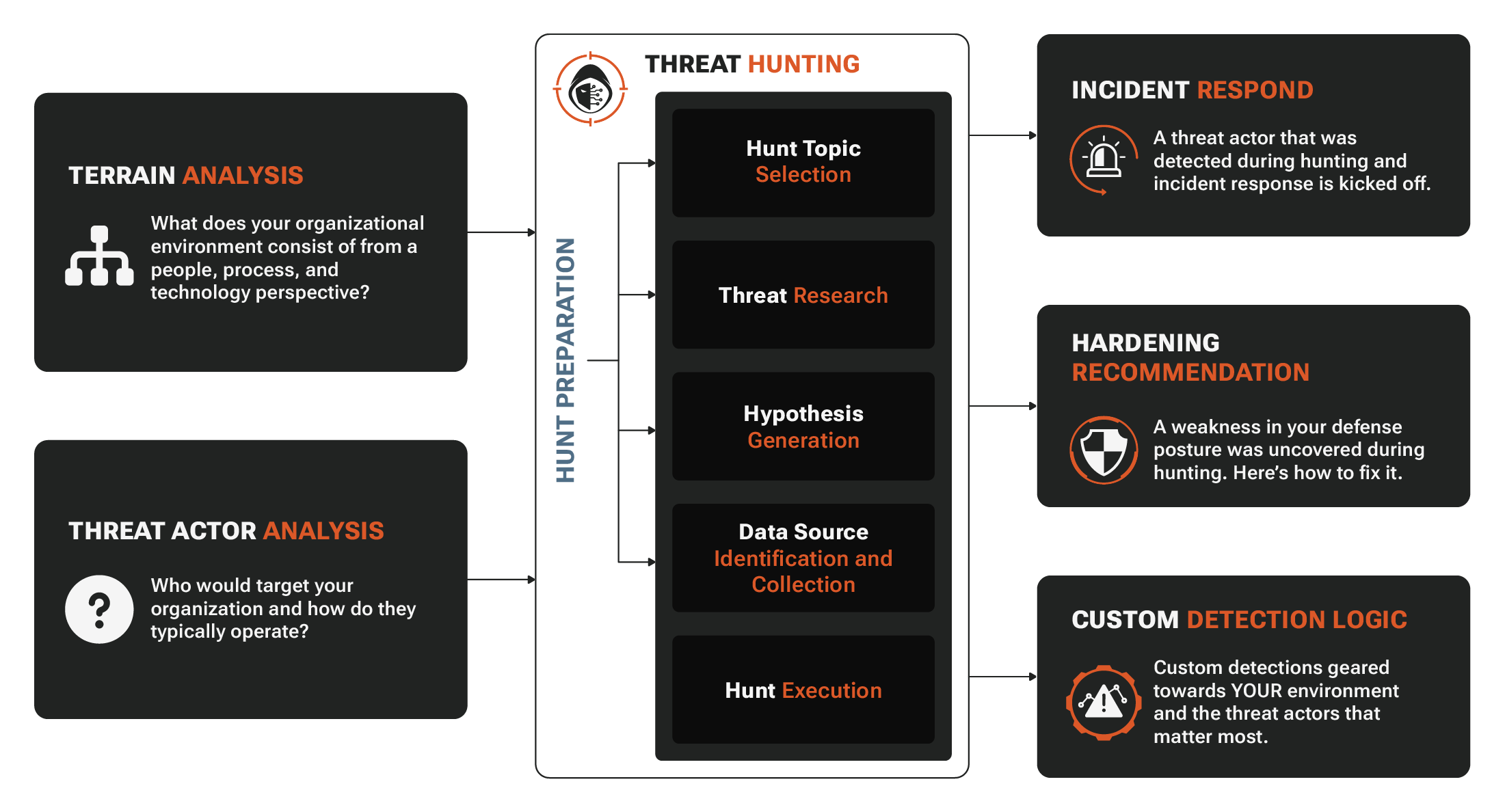
RADICL Threat Hunting: How it works
Terrain Analysis
Map your people, process, and tech to baseline telemetry (endpoint, identity, network threat detection).
Threat Actor Analysis
Prioritize who targets SMBs and DIB contractors and how they operate (initial access, persistence, lateral movement).
Deep Embedded Threat Hunting
Analyze historical data to find embedded threats operating below alert thresholds.
Full-Spectrum Continuous Detection Analytics
Threat intelligence infused, real-time and continuous analysis of log and telemetry data looking for known and novel indicators of active compromise.
Complete Incident Response
When threats are discovered: immediate containment, thorough eradication, full recovery, and go-forward attacker return analytics.
Frequently Asked Questions
Standalone tools like EDR and SIEM are the building blocks of defense in depth, but they only deliver value when a skilled team manages them day to day. Cybersecurity-as-a-Service (CSaaS) providers go further by combining expert operations with their own proprietary technology stack, delivering a fully managed threat detection and response solution. Instead of leaving SMBs to juggle multiple tools and platforms, CSaaS provides continuous threat hunting and monitoring out of the box. At RADICL, we also support side-by-side operations, giving customers access to the same platform and toolset our analysts use, creating a best-of-both-worlds model that builds true cyber resilience.
We do both and more. RADICL delivers continuous cybersecurity threat monitoring alongside full managed detection and response. That means we don’t just raise alerts; we take ownership of incidents end to end, from containment and eradication to recovery and lessons learned. Unlike providers that stop at monitoring, our Cybersecurity-as-a-Service (CSaaS) platform combines proprietary defense-in-depth tools with expert threat hunters to deliver true cyber resilience for SMBs and defense contractors.
Traditional MDR waits for alerts. RADICL delivers proactive and continuous threat hunting. Our Embedded Threat Hunting uncovers evidence of threats already operating and flying under the radar through “living off the land” techniques. RADICL’s proprietary Continuous Detection Analytics combine threat intelligence with ongoing analysis of log and telemetry data to identify both external and internal attacks enabling rapid response to new or spreading compromises.
Yes. RADICL delivers full-scope managed threat detection and response with weekly proactive hunting, 24/7 incident ownership, and coverage across endpoint, identity and network. We don't forward alerts---we investigate, contain, and eradicate. We monitor, detect, and operationally own the end-to-end incident response process - 24/7.
24/7 response with complete incident ownership. Unlike traditional MDR that forwards alerts, we immediately begin containment and eradication when threats are discovered through hunting or alerts.
Yes. RADICL’s threat hunting and incident response services generate auditor-ready evidence for frameworks such as NIST CSF, NIST 800-171, and CMMC. Every investigation and response includes full compliance documentation, helping SMBs and defense contractors demonstrate controls, reduce audit prep time, and prove ongoing cyber resilience.
Defense in depth is a cybersecurity approach that uses multiple security layers to ensure proactive and reactive protections are in place. Defense-in-depth accepts that errors will occur in IT operations (i.e., opening a back door) and that people will make mistakes (i.e., clicking on a phishing email). Defense-in-depth accepts that motivated threat actors will find a way to bypass the front line of defenses via known or novel attack methods. Defense-in-depth counters this by taking a layered security approach, ensuring that if one layer fails, another can impede and/or detect the threat.
RADICL's defense in depth architecture takes a "Harden-Detect-Respond" approach. We harden the IT infrastructure through best-in-class managed EDR and proactive vulnerability management. We harden people through security awareness training. If a threat somehow bypasses protections, we ensure it is detected via DeepSpectrum threat hunting and quickly eradicated through end-to-end incident response ownership.
Ready to Stop Managing Security and Start Running Your Business?
RADICL delivers enterprise-grade cybersecurity through AI-powered automation and human expertise — purpose-built for SMBs facing nation-state threats.